Azure & AWS: Site-to-Site VPN
- 4 minsINTRODUCTION
Azure provides a how-to guide for how to create a Site-to-Site VPN in their technical documentation here: Product Directory -> Azure -> VPN Gateway -> Create a Site-to-Site.
AWS provides a how-to guide for how to create a Site-to-Site VPN in their technical documentation here: AWS Documetation -> VPN -> AWS Site-to-Site
I was curious to see what this would look like, so I decided to set this up in my test lab and run through the process my self. I documented the steps below.
WHAT IS A SITE TO SITE VPN?
A site-to-site virtual private network (VPN) is a connection between two or more networks, such as a corporate network and a branch office network. A site-to-site VPN is a permanent connection designed to function as an encrypted link between offices (i.e., “sites”). This is typically set up as an IPsec network connection between networking equipment.
GOOD TO KNOW
- AWS supports certificates for Internet Key Exchange (IKE) authentication. To use certifiates for IKE Authenitcation, you must first create a subordinate Certificate Authority (CA). See here for more details.
HOW DO YOU SET UP A SITE-TO-SITE VPN?
Now that we know the key benefits and the important terminology, we are better prepared to dive into the Site-to-Site VPN deployment process.
DEPLOYMENT PROCESS OVERVIEW
- Create a Virtal Network Gateway in Azure.
- Create a Virtual Private Gateway in AWS.
- Attach the Virtual Private Gateway in AWS to a Virtual Private Cloud in AWS.
- Create a Customer Gateway in AWS for Azure.
- Create a VPN Connection in AWS.
- Create a Local Gateway in Azure.
- Create the Connection in Azure.
- Update the Routing Table in AWS.
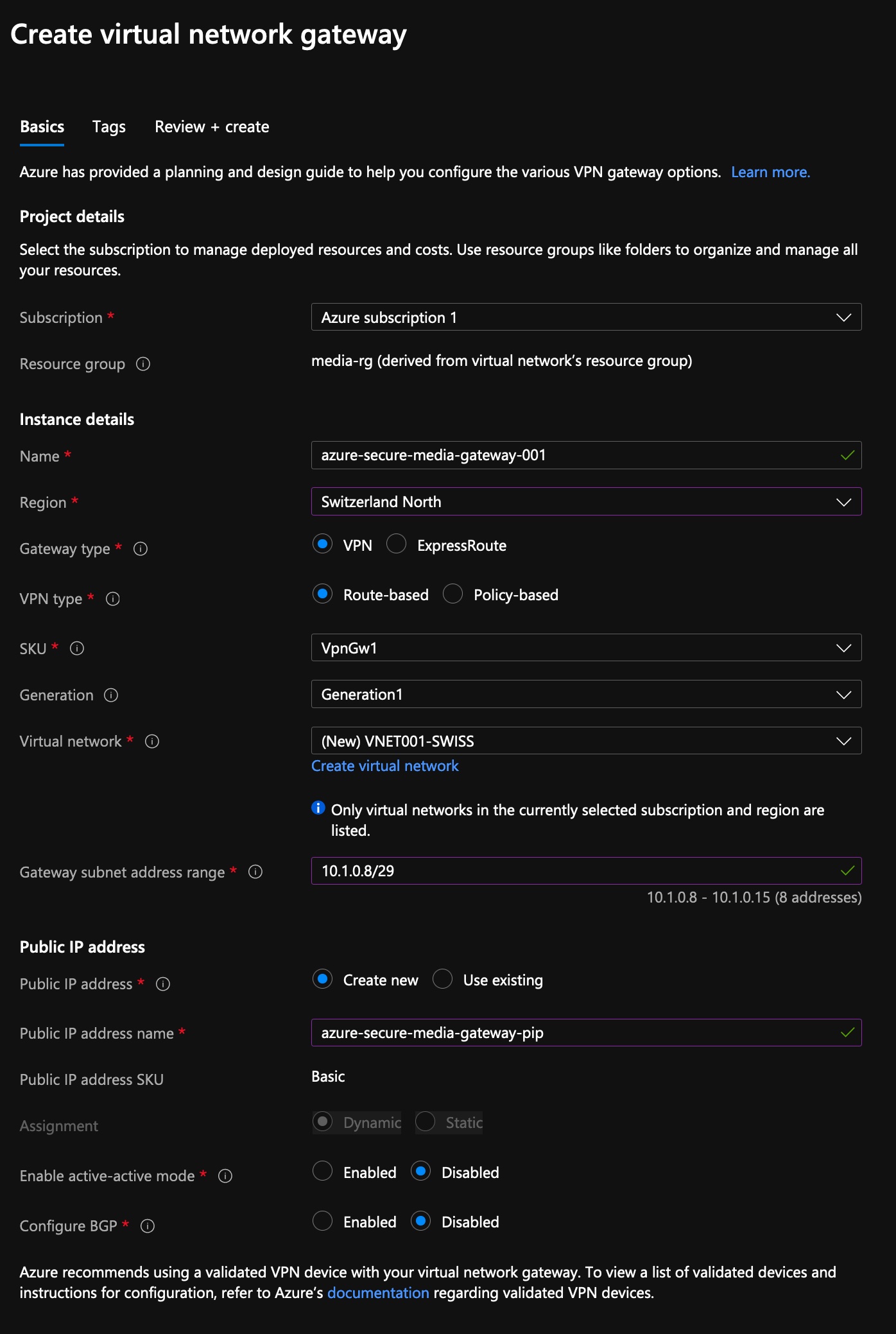
CREATE A VIRTUAL NETWORK GATEWAY IN AZURE
- Sign in to the Azure portal
- Click on create resource and search for Virtual Network Gateway.
- Click Create
- Fill out fields.
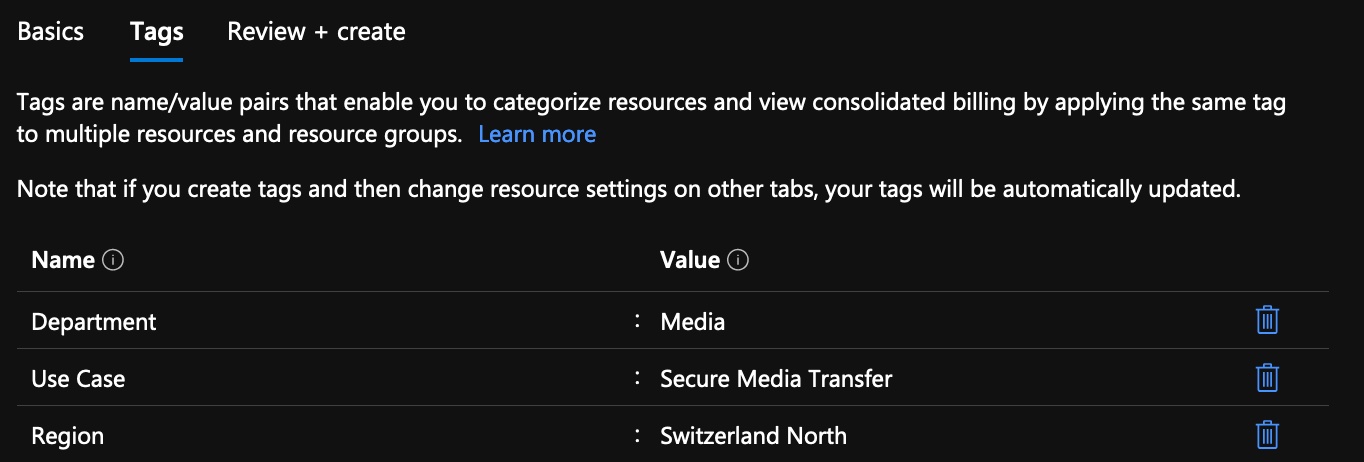
- Tag your resources appropriately.
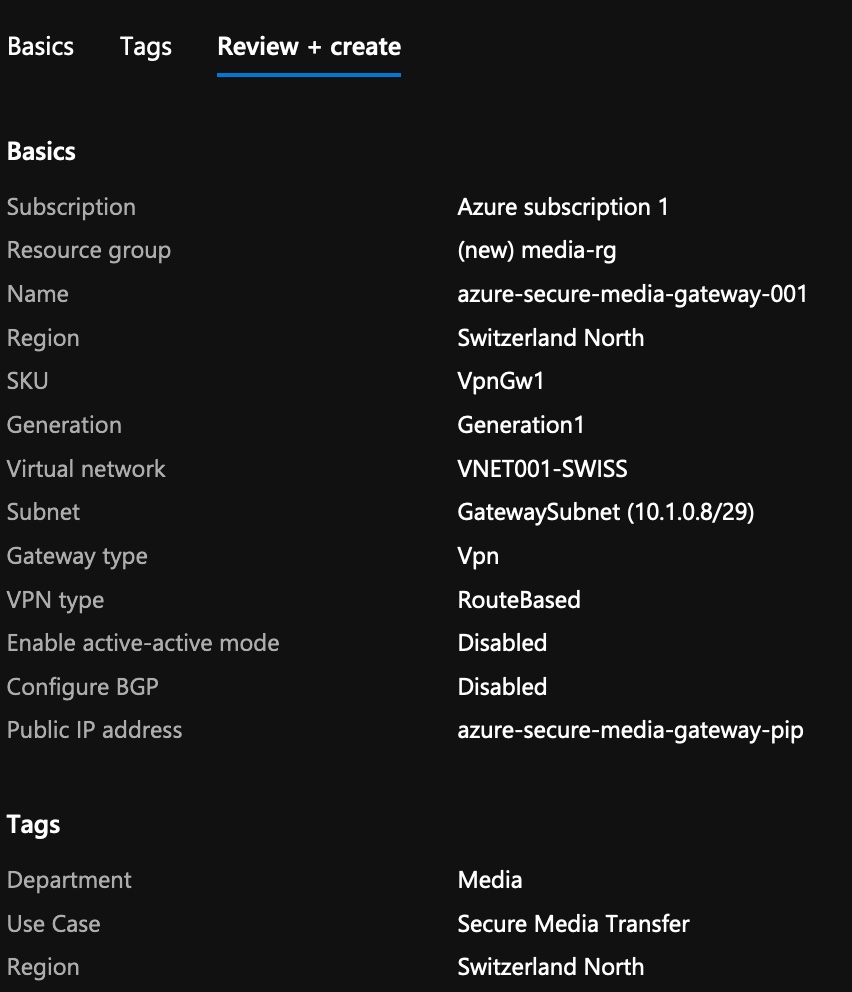
- Review and create the Virtual Private Gateway.
CREATE A VIRTUAL PRIVATE GATEWAY IN AWS
- Sign in to the AWS Console
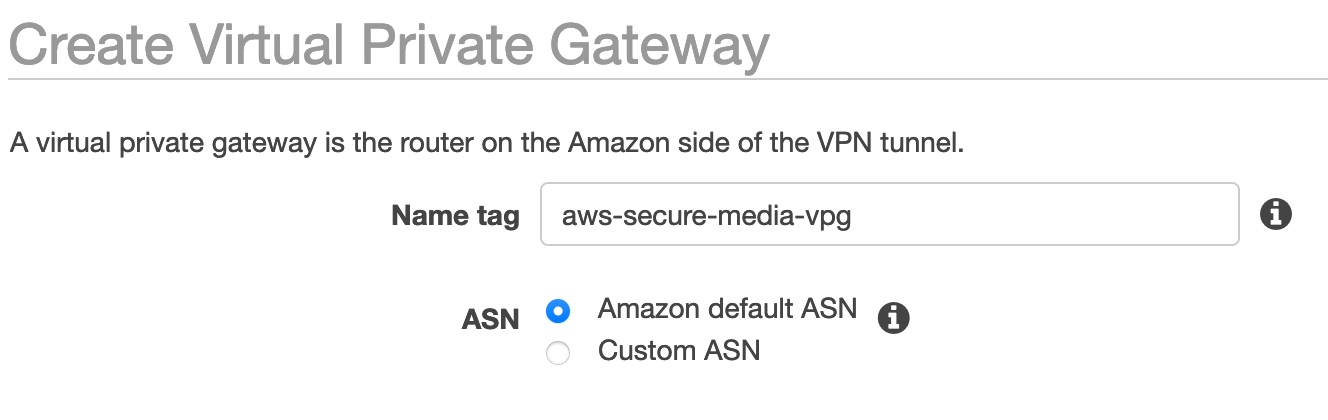
- Navigate to Virtual Private Gateways -> Create Virtual Private Gateway
- Name your Virtual Private Gateway and click Create.
CREATE A VIRTUAL PRIVATE GATEWAY IN AWS
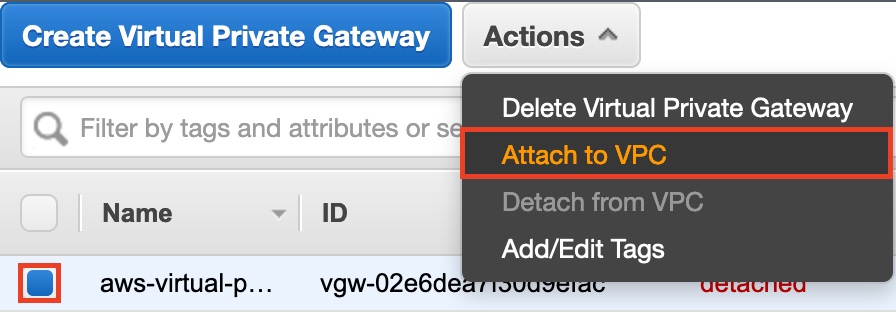
- Click on your newly created Virtual Private Gateway and attached it to your Virtual Private Cloud.
CREATE A CUSTOMER GATEWAY IN AWS FOR AZURE
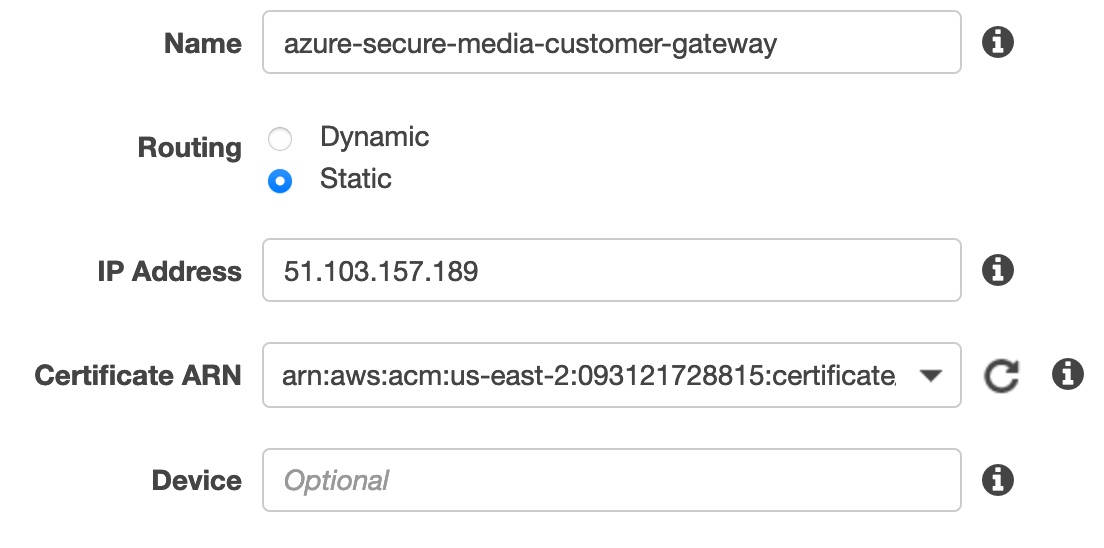
- In your Virtual Private Cloud Dashbord, click Customer Gaweways.
- Fill out the Name, IP Address, and choose your Certificate ARN.
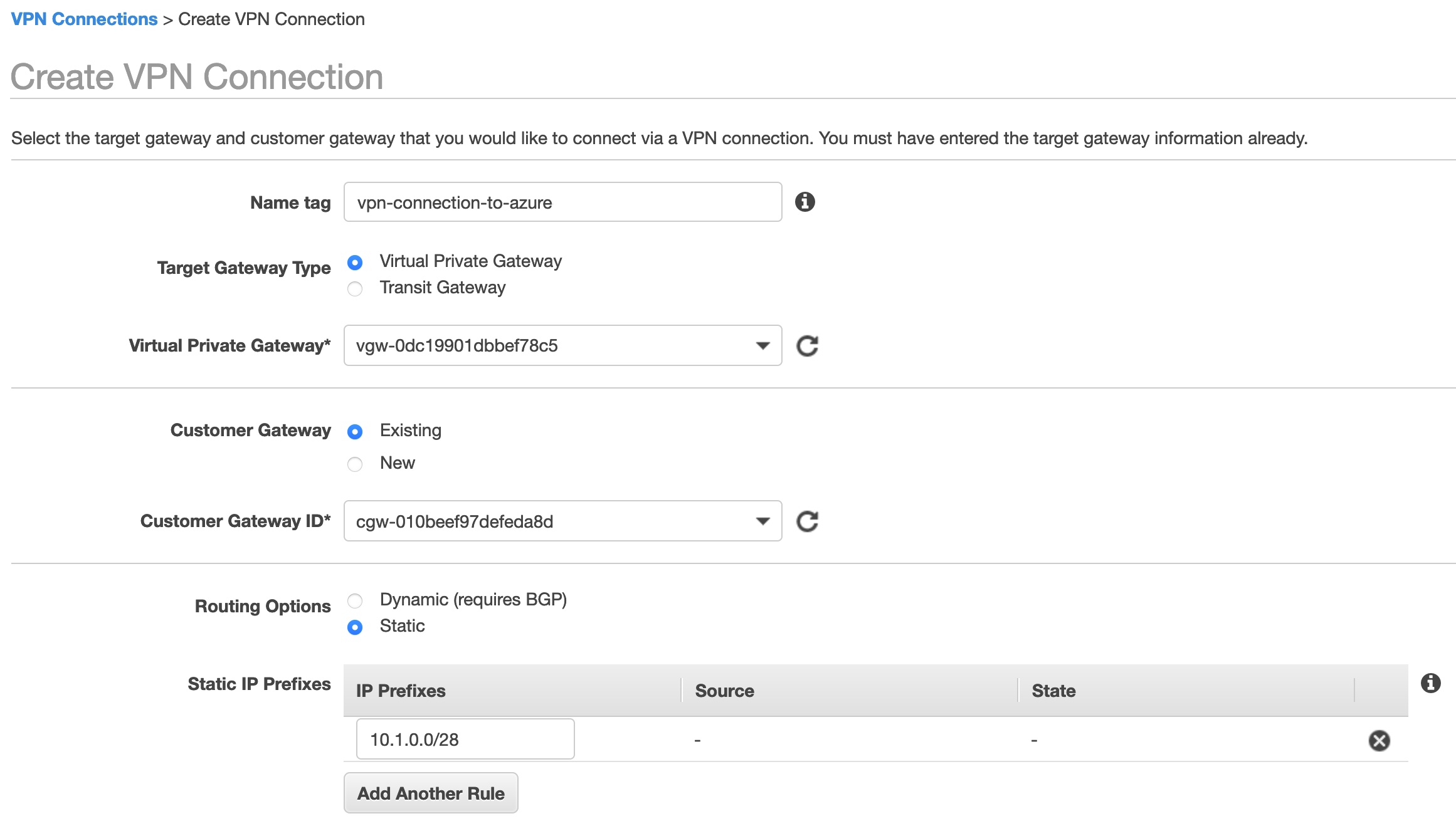
CREATE VPN CONNECTION IN AWS
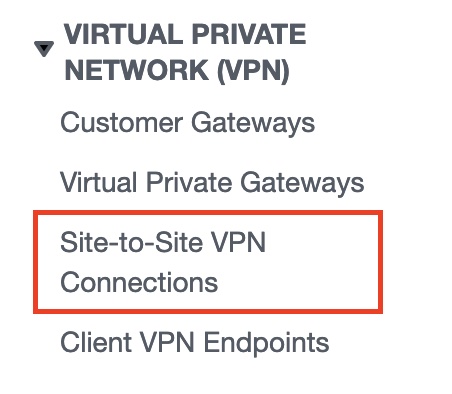
- Select Site-to-Site VPN Connections from the left Menu Bar.
- Enter the details, alpong with the Virtual Private Gateway and Customer Gateway created earlier. In this example, I am using the static routing so I added the CIDR block from my Azure VNET. Leave all other fields default.
- Download the configuration file as follows:
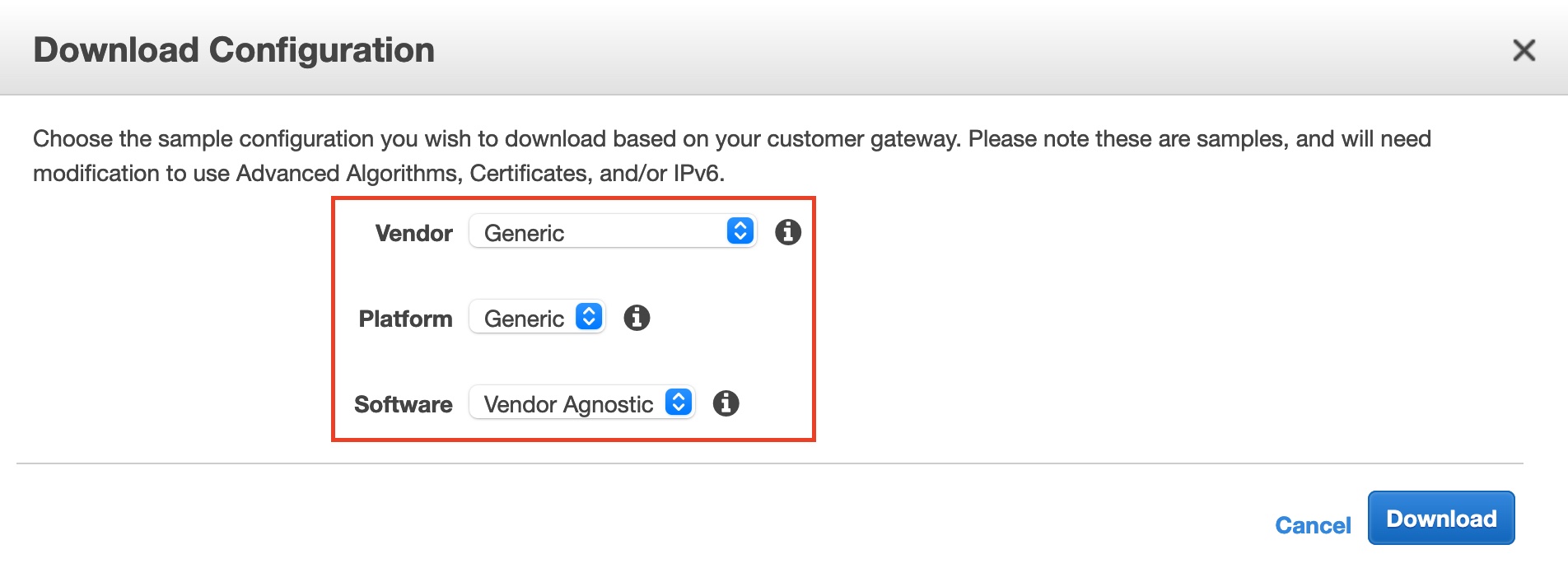
CREATE A LOCAL GATEWAY IN AZURE
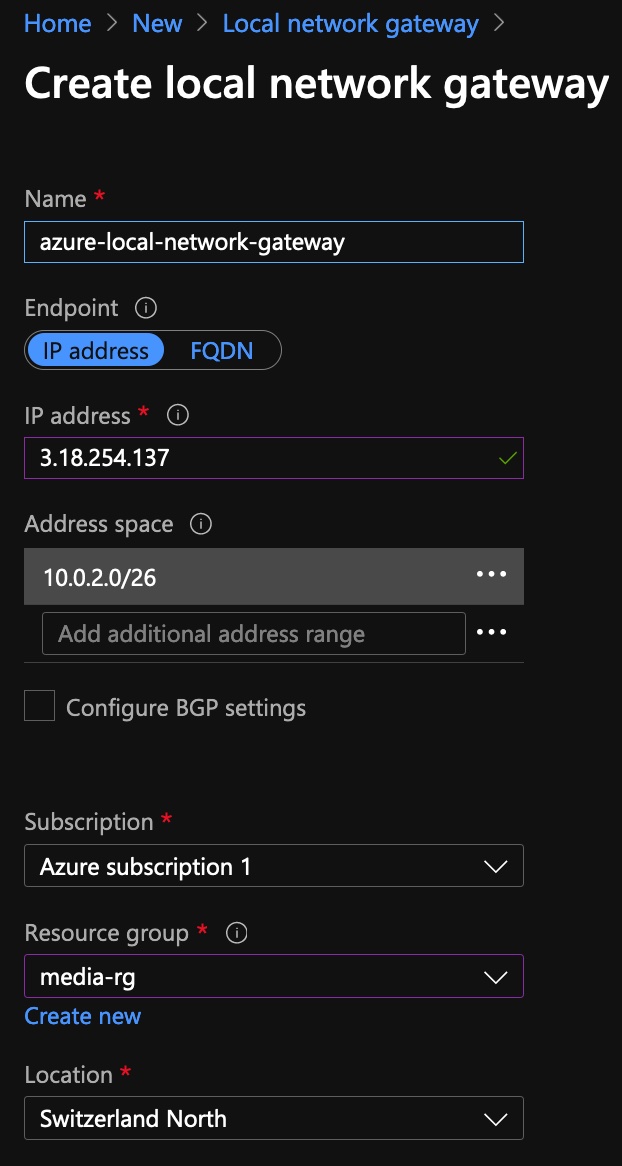
- Back in the Azure portal, search for Local Network Gateway and click Create
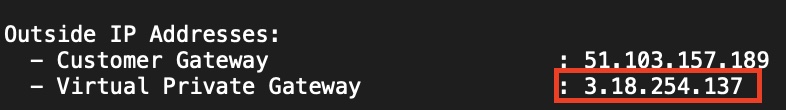
- Fill out the fields. Use the IP Address under Outside IP Adresses -> Virtual Private Gateway
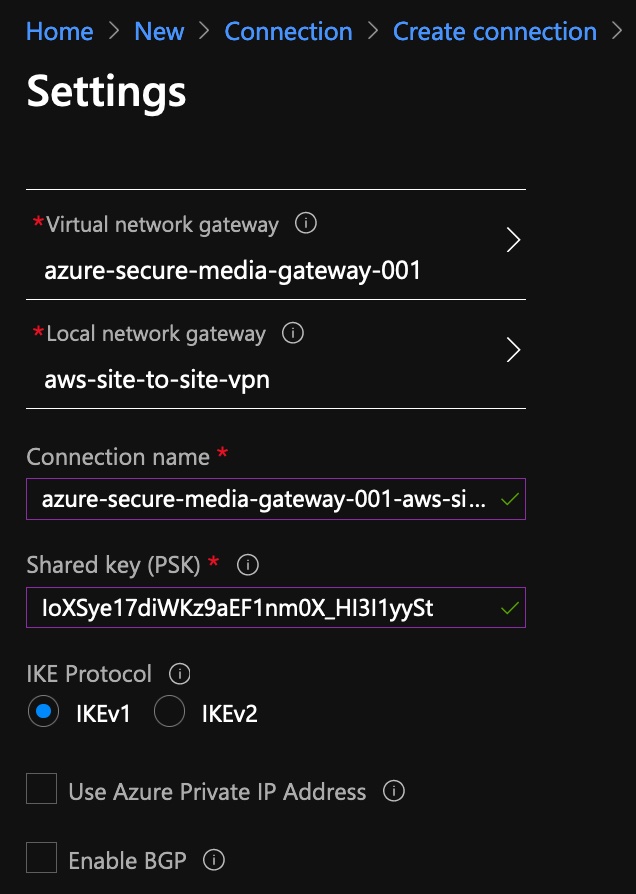
CREATE A CONNECTION IN AZURE
- In the Azure portal, search for Connection and click Create
- Select the appropriate Connection Type, Subscription, Resource Group, and Location and click OK.
- Select the Virtual Network Gateway and Local Network Gatewway created earlier and enter the PSK from the configuration file. Set the connection name
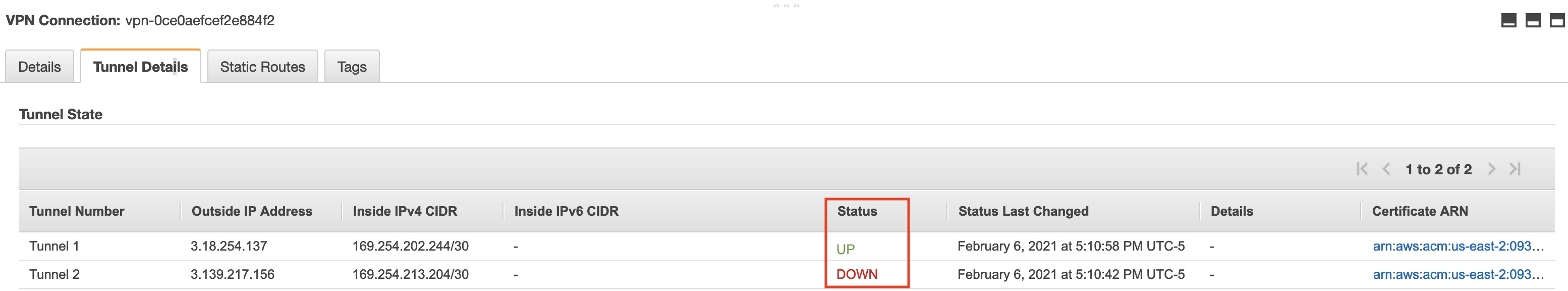
- After the deployment succeeds, the tunnel should be established. To verify this, go to the connection and check the status.
- Verify the status of the tunnel in the AWS Console:
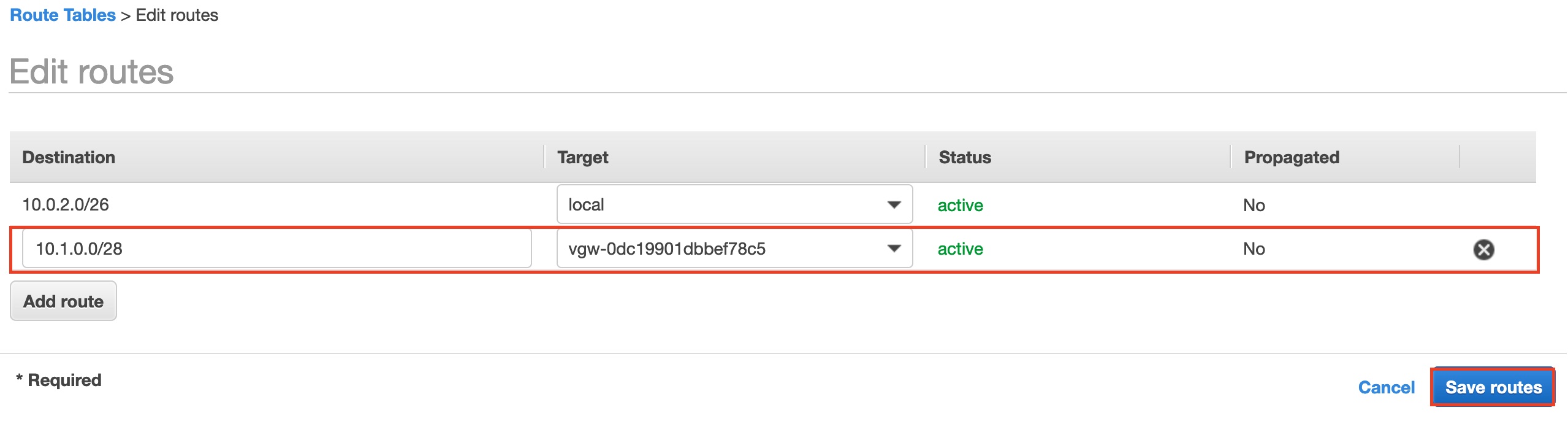
UPDATE THE TOURING TABLE IN AWS
- Search for Route table in your AWS Console.
- Edit the routing table to include the CIDR block from your Azure Virtual Private Gateway, this will ensure any traffic destined for the Azure network will route through the Virtual Private Gatewaye rather than going out of the internet gateway.