
TCP Connections & Proxychains
- 4 minsINTRODUCTION
A proxy server is a dedicated computer or software system running on a computer which can act as an intermediary between an end device, such as a computer and another server which a client is requesting any services from. If you use Proxchains and connect to the Internet, your client IP address will not be shown but rather the IP of the proxy server.
WHAT IS PROXYCHAINS
Proxychains is a UNIX program that forces any TCP connection made by any given application to go through proxies like TOR or any other SOCKS4, SOCKS5 or HTTP proxies.
IMPORTANT TERMINOLOGY
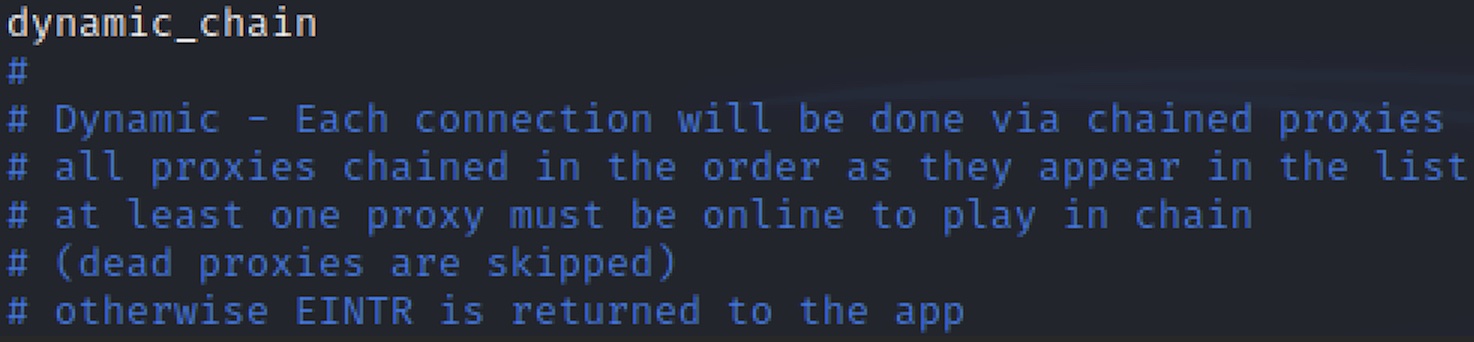
- Dynamic Chain — dynamically runs through all available proxies. All proxies must be online to play and dead proxies are automatically skipped.
- Strict Chain — follows a connection of proxies in sequences. All proxies must be online to play and a single dead proxy in the chain will result will interrupt the connection.
- Random Chain — bounces connection back and fourth between random proxies. Best for testing your IDS o not for production.
IMPORTANT CONCEPTS
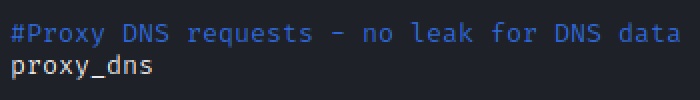
- DNS Leak - DNS queries must also be proxied, if not your privacy is at risk since all DNS queries are sent using an unencrypted DNS request over the network.
In this example, I go through the process of configuring Proxychains on Kali Linux.
REQUIREMENTS
- Unix OS
DEPLOYMENT PROCESS OVERVIEW
- Verify Current Environment
- Configure proxychains.conf File
- Verify Configuration
TIME TO IMPLEMENT: 15 minutes
VERIFY CURRENT ENVIRONMENT
It is important to verify your current environment before begin using proxychains. After we congifure Proxychains, we can use the following information to verify Proxychains is functioning appropriately.
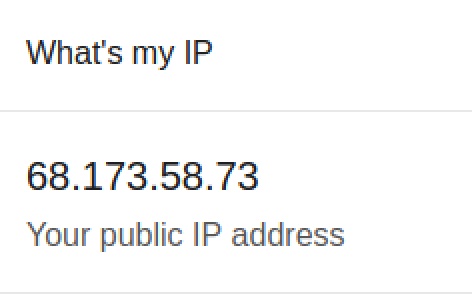
- Go to google.com and search the following. Take note of your public IP address:
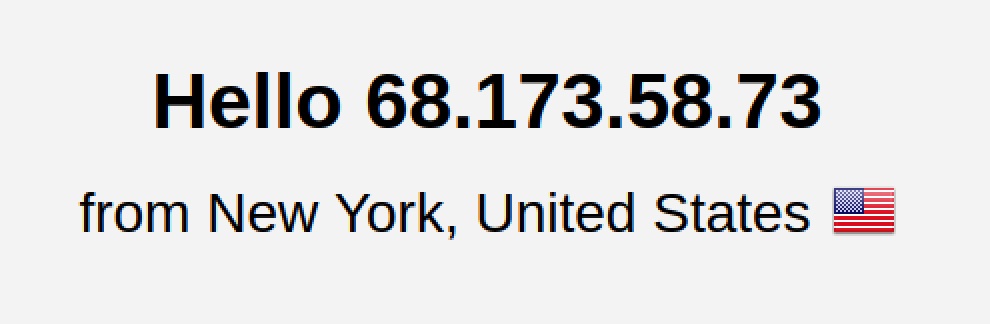
- Go to the following URL and take note of the IP your DNS Server is reporting for you. It should be same IP from the first step.
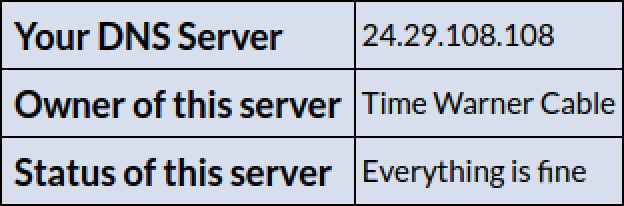
- Now, go to the following URL and take note of your DNS Server's IP address:
- Change directories to Documents. Here, we will make a file to keep trake of the IP addresses we just took note of.
- Create a file and call it environment by running the following command:
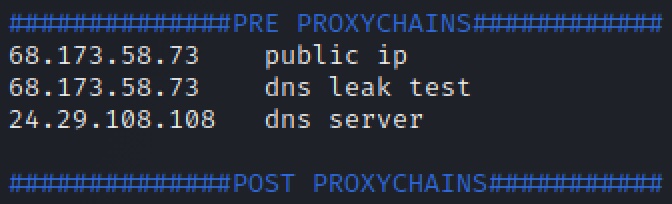
- Open the file with the following command then paste IP addresses along with their counterpart.
What's my ip?
https://dnsleaktest.com/
http://www.whatsmydnsserver.com/
cd ~/Documents
touch environment
vim environment
CONFIGURE PROXYCHAINS.CONF FILE
- Open the proxychains.conf file in vim on Kali Linux by issuing the following command:
- In the /etc/proxychains.conf configuration file, enable the option for dynamic chain:
- Scroll down and enable the option for Proxy DNS Requests:
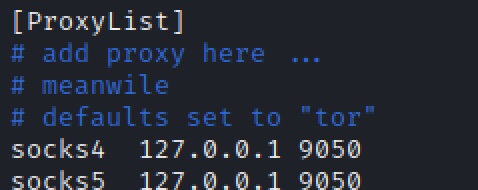
- At the botom of the configuration file add the following to enable SOCKS5 and Tor:
- If you haven't already, install Tor by running the following command:
- Start the Tor service and check it's status after by running the following commands:
sudo vim /etc/proxchains.conf
socks5 127.0.0.1 9050
sudo apt-get install tor
service tor start service tor status
VERIFY CONFIGURATIONS
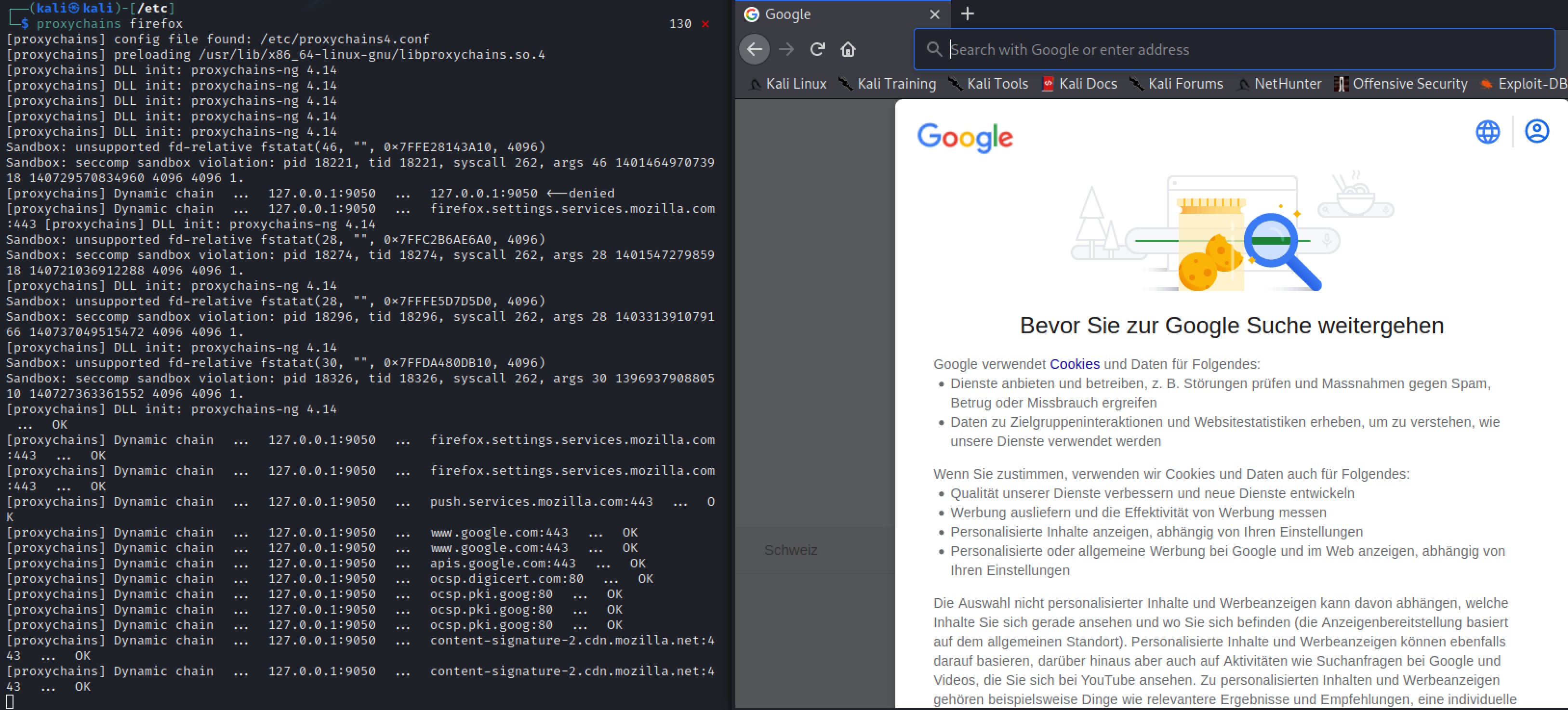
- Run the following command to test using Firefox with the new Proxychains configuration. Firefox will open.
- Go to google.com and search the following. Take note of your public IP address:
- Go to the following URL and take note of the IP your DNS Server is reporting for you:
- Now, go to the following URL and take note of your DNS Server's IP address:
- Change directories again to Documents. Here, we will make note of the IP addresses after our Proxchains configuration so we can compare the differences.
- Paste each new IP address in and compare.
proxychains firefox
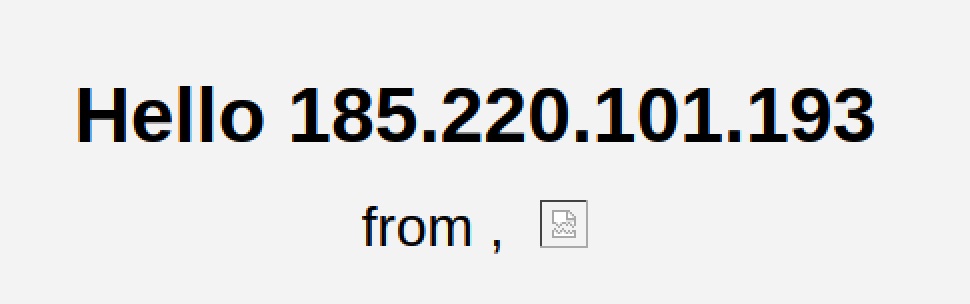
Note the dynammic chain configuration in Terminal and how the browser opens up in German:
What's my ip?
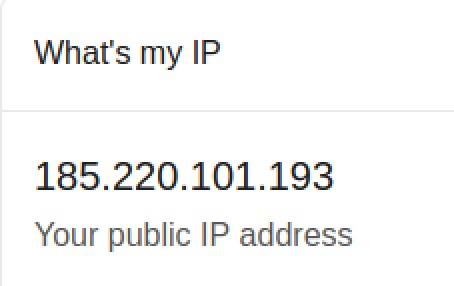
https://dnsleak.com/
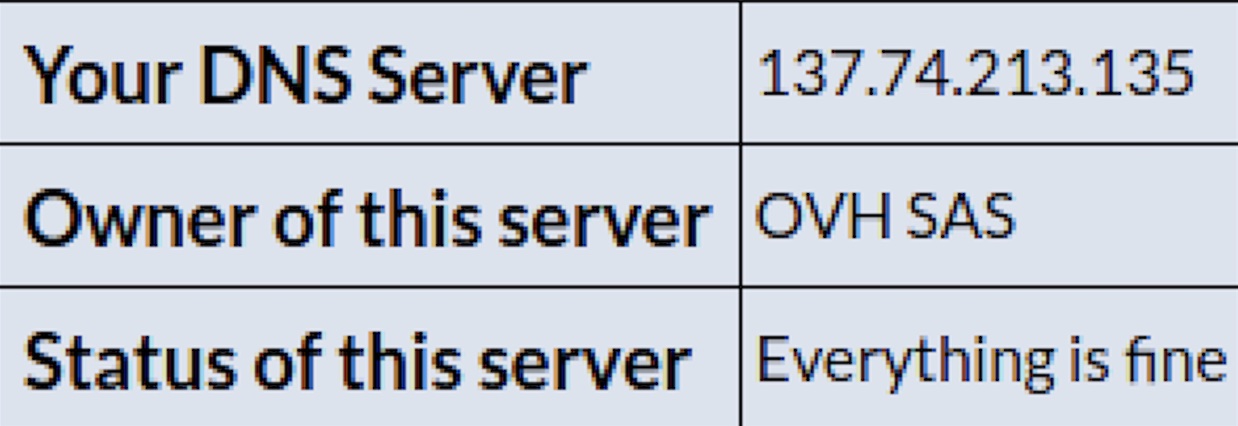
http://www.whatsmydnsserver.com/
cd ~/Documents vim environment
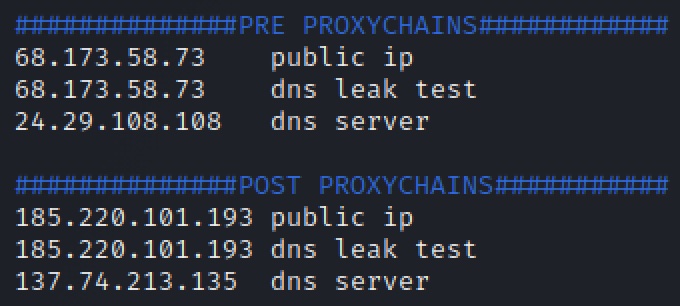
By looking at our environment file, we are able to verify that Proxychains is (1) forwarding our IP address through Tor proxy, (2) our DNS quieres our proxied through Tor (and mitigating DNS Leak), and (3) our DNS server is reporting a different IP address. Proxychains is configured properly.
USE CASES
See below for some exampe use cases for Proxychains:
- Proxychains with Nmap scans:
- Proxychains with SSH:
proxychains [nmap command] proxychains nmap -sC -sV -oA nmap/outputfile 10.10.10.10
ssh -D 127.0.0.1:8080 target.com
This will make SSH forward all traffic sent to port 8080 to target.com. You will need to add 127.0.0.1:8080 to the Proxychains proxy list.
SUMMARY
- The concept of proxies and knowing how to use proxies is important to learn for anyone in infosec.
- Having the Proxychains tool configured and ready for use can prove useful, even if you don't use the tool daily.
- Be sure to double check your configurations - a DNS leak can easily expose your identity.